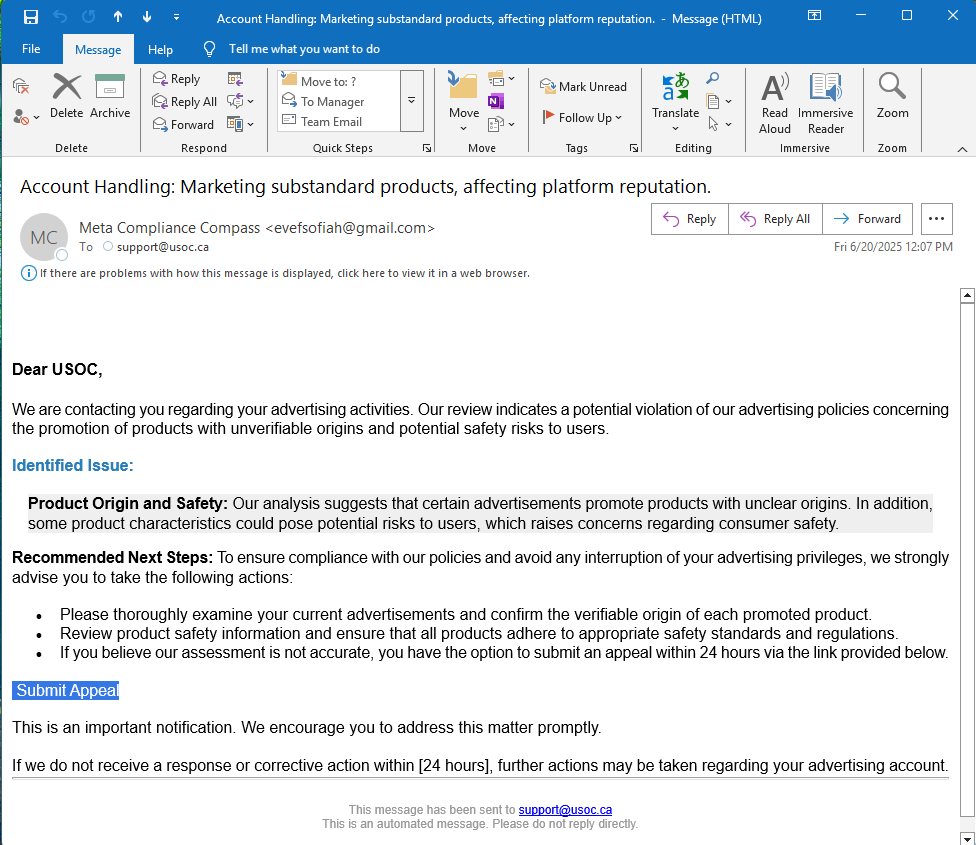
On June 20, 2025, a phishing attempt was directed at [email protected], disguised as an official compliance warning from a so-called “Meta Compliance Compass.” The email falsely claimed that our Facebook advertisements violated safety policies and urged us to click a link to “Submit Appeal”—a classic phishing trick.
What We Observed:
Return Path: [email protected] (clearly a free email, not an official domain)
Subject: Misleading and intimidating, urging quick action
Language: Professional-sounding text warning about unverifiable products
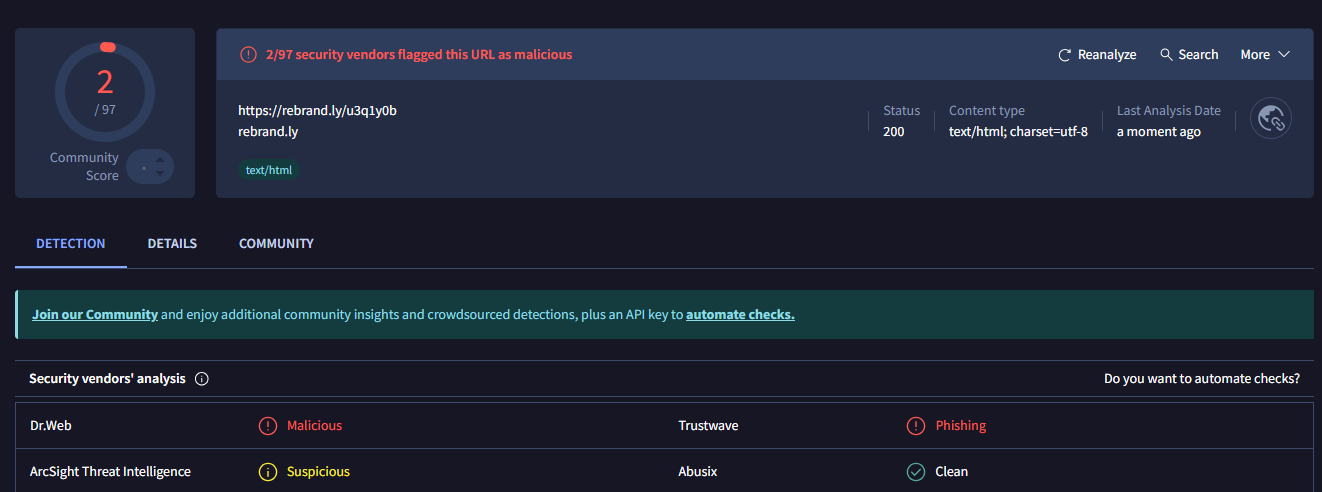
Shortened Link: https://rebrand.ly/u3q1y0b – masked malicious URL
Destination Link: https://gannezoiproubri.vercel.app/bkavjcn.sbkxjhsbjbns
Headers & Source: Sent from a personal IP address in the U.S., not a verified Meta server
Why This Is Dangerous:
Phishing emails like this aim to:
- Steal credentials by tricking you into logging into fake portals
- Install malware through malicious links
- Create panic using legal or compliance-sounding language
Despite appearing legitimate (passing DKIM, SPF, and DMARC checks), it came from a Gmail account, not a verified business domain—an immediate red flag.
What You Should Do:
- Never click on suspicious links without hovering to inspect the URL.
- Verify senders — Official companies don’t use free email services for compliance warnings.
- Report phishing to your IT or cybersecurity team immediately.
- Use email filtering tools and SpamAssassin to score and block suspicious emails.
USOC Inc.'s Commitment
We treat every phishing attempt seriously and actively monitor threats. If you're a business owner or employee receiving suspicious emails, do not respond. Instead, reach out to us — we can help audit and secure your systems.
Have questions about how to protect your business from phishing attacks?
Reach out at https://usoc.ca/contact for affordable, jargon-free cybersecurity support.